Services
Dara Security offers a wide range of services designed with security in mind.
Compliance & Risk Management
Profiling &
Penetration Tests
Compliance & Risk Management
PCI DSS Validation:
PCI DSS compliance shows that an entity adheres to the Payment Card Industry Data Security Standard (PCI DSS), a standard that incorporates security best practices and aims to protect customer payment card data. Compliance is not a one-time event but an ongoing process guided by a PCI-certified Qualified Security Assessor (PCI QSA).
Regardless of size, all organizations that process, store, or transmit payment card data must comply with the PCI DSS. Compliance efforts range from completing a PCI questionnaire to conducting an on-site PCI DSS audit.
Dara Security has over 40 years of combined industry experience, multiple certifications, and a growing list of client references that has earned us the trust of companies worldwide. With our extensive experience in PCI DSS Validations, we are pleased to offer this service with our partner, Certify Audit Services, an established information security company certified by the PCI Council.
PCI P2PE Validation
The Importance of Encryption:
As the number of reported security breaches continues to rise, many individuals and businesses are asking what can be done to further defend against cyber crime. One approach that has drawn much attention lately is encryption. By encoding messages so that only authorized parties can read it, information is kept more secure.
About P2PE and Security Encryption:
Major internet players have coordinated efforts to provide their users full encryption of information accessed and sent. In addition, businesses are pursuing an extra layer of security by requiring payment card data to be encrypted at the point of interaction, an approach known as Point-to-Point Encryption, or P2PE.
In P2PE, cardholder data is encrypted as it travels through the transaction process, from the POS to the processor/acquirer. The business has no ability at all to decrypt this cardholder data. Contrast this scenario to the business that has no P2PE in place. Without P2PE, cardholder data is not encrypted at the POS, and the business has access to this data throughout the transaction process.
Using a Certified P2PE Security Firm:
In an effort to increase security, reduce risk, and limit liability, many businesses are pursuing P2PE. In fact, many of our clients have requested P2PE validation in addition to their annual PCI audits. As a result, Dara Security is pleased to offer the PCI P2PE Validation service with our partner, Certify Audit Services, an established information security company certified by the PCI Council.
PCI PIN Audit:
Organizations desiring to comply with the requirements of participating card brands should have a PCI PIN Audit performed by a PCI Qualified PIN Assessor (PCI QPA). The PCI PIN Audit is conducted using the PCI PIN Security Standard which is for the secure management, processing and transmission of PIN data at ATMs and attended/unattended point-of-sale (POS) terminals.
By utilizing a PCI QPA company to conduct the PCI PIN assessment, a merchant or service provider can be confident that:
- the auditor has the required skills and experience to conduct an accurate assessment
- the company has processes for protecting a client’s confidential information
- the company has client references from relevant security assessment engagements
Dara Security is pleased to offer the PCI PIN Audit service with our partner, Certify Audit Services, an established information security company certified by the PCI Council to conduct PCI PIN Audits using the latest version of the PCI PIN Security Standard.
HIPAA Gap Assessment:
The Health Information Portability and Accountability Act (HIPAA) was enacted in 1996 to address the security and privacy of health care data. In addition, the Health Information Technology for Economic and Clinical Health Act (HITECH Act) was enacted as part of the American Recovery and Reinvestment Act of 2009 (ARRA) and signed into law on February 17, 2009. The HITECH Act amended HIPAA with significant changes to data breach notification, enforcement, and penalties.
Covered Entities:
Covered entities, such as hospitals and healthcare providers, have been required to comply with the Health Information Portability and Accountability Act (HIPAA) since 1996. Service providers (a.k.a., Business Associates or BAs) for these covered entities likely had a contractual obligation to comply with HIPAA, but as of September 23, 2013 (Omnibus Rule under HITECH refinements), these service providers are also required to be covered directly under HIPAA. In other words, business associates to hospitals and healthcare providers are now contractually obligated and legally required to comply with HIPAA as they are now considered covered entities.
HIPAA Gap Assessment:
To quickly identify these gaps and firmly establish a roadmap for compliance, Dara Security created a HIPAA Gap Assessment to review systems and processes to identify areas of non-compliance. The HIPAA Gap Assessment is performed against selected services, applications, and infrastructure within an organization. It reviews current privacy measures, as well as security controls against HIPAA by:
- Documenting your level of regulatory compliance
- Identifying HIPAA Program vulnerabilities and weaknesses
- Providing independent verification of the effectiveness of existing controls
- Reducing the organization’s privacy and security costs
- Offering insight into industry best practices
In return, you will:
- Greatly minimize risk by quickly benchmarking against HIPAA/HITECH to identify non-compliant areas
- Streamline the remediation process
- Reduce the cost, confusion, and complexity of HIPAA/HITECH compliance
- Provide regulators and business partners evidence that your organization has taken a risk-based approach to quickly attain HIPAA compliance
- Avoid damages often totaling millions of dollars that could result from a protected health information (PHI) compromise
- Add value to your overall compliance program by engaging a non-partisan third-party professional partner
Dara Security Experts:
Dara Security's consultants are experts in understanding both the technical aspects and the business components of your organization. Our experienced Team Members have worked with many organizations in the commercial, government, and health and human services sectors, including providers and service organizations. As part of these relationships, Dara Security has gained extensive knowledge and experience with National Institute of Standards and Technology (NIST) security control frameworks, such as NIST SP 800-66 [PDF], that are commonly used in government agencies and can be adopted by commercial organizations for determining their compliance with the HIPAA Security and Privacy Rules.
Information Security Review:
Security is no longer simply a matter of protecting one's own organization, but has evolved to include how an organization protects the data entrusted to it by consumers, employees, and third-parties. One of the difficulties every organization faces is determining exactly where it stands with regard to security. Furthermore, most organizations find themselves dealing with at least two different compliance frameworks from regulations, contracts, or organizational standards. An audit around a regulatory standard, such as the PCI DSS, will give a clear picture of what needs to be done to meet that regulation. Meanwhile, a penetration test shows how much work is needed for a skilled attacker to compromise your IT systems by acting on a subset of your available vulnerabilities.
Questions:
But where does the organization as a whole stand as far as information security review and compliance? Did you know that generally there is at least a 70% overlap between security and IT frameworks and are you duplicating efforts by evaluating each individually? What has the greatest value to your organization and is it well protected? To answer these questions, a more business-focused and holistic view is necessary.
Process:
Dara Security uses the SANS 20 as a basis to map into one control framework the various organizational compliance mandates (PCI DSS, HIPAA, State, etc.) that affect your organization. This process is coupled with a risk assessment that identifies and assesses risks that could impact business objectives, resulting in a useful, holistic foundation for your organization’s security program. Performing this information security review assessment on an annual basis, Dara Security provides you with a clear view of your organization’s security program: its current state, how it has changed over time, and where your organization stands with required mandates. Controls are precise and carefully designed so that your business can continue meeting your goals without distraction. Our recommendations provide essential and useful information, and ultimately add value to the business by ensuring your organization’s data is appropriately protected.
What We Can Do For You:
Our methodology has been employed to assess small, private organizations of fewer than 100 employees, as well as Fortune 500 corporations with thousands of employees. Our consultants are experts in understanding both the technical aspects as well as the business aspects of your organization. You can schedule an information security review with the Dara Security team today.
Profiling &
Penetration Tests
Red Team Exercise:
Dara Security's Red Team Exercise is a systematic and realistic assessment of a client's environment that will assist the client in identifying, responding to, and containing an adversarial attack.
Our red team operators will simulate the actions of a sophisticated threat actor operating from an assumed compromise scenario. The exercise will start with access to a pre-compromised device within a client's internal network and will focus on testing a client's ability to detect, respond to, and mitigate advanced adversarial activity.
Our team will develop a targeted attack plan, secure an initial foothold and attempt to escalate privileges within the network, aiming to access higher levels of control over critical systems. Using the compromised device as a pivot point, we will move laterally through the network and employ techniques to mimic real-world adversaries while avoiding detection. Once high-value assets are identified, we will simulate the completion of an adversary's objectives and achieve other goals defined during project planning.
Penetration Testing:
Penetration Tests, or ethical hacking, are an important part of any security program. Our methodology, based largely on the Open Source Security Testing Methodology (OSSTM), is designed to validate the security surrounding externally connected systems from the Internet, as well as within a Corporate Network, depending on your needs.
Both External and Internal Penetration Tests are designed to detect weaknesses in a system, network or application that could allow host or information compromise and safely exploit these weaknesses to evaulate the impact on business operations.
External Pentesting:
External Penetration Testing involves finding and exploiting known and unknown vulnerabilities from the perspective of an outside attacker. External pentests can also test an organization's monitoring and incident response capabilities. Our testing is designed to mimic a variety of scenarios including a casual hacker who infiltrates a system for spam or other unrelated malicious purposes, dedicated hackers targeting with a specific goal and rogue employees or disgruntled ex-employees who may have privileged access or the ability to bypass certain access controls.
Using the Open Source Security Testing Methodology, our tests are comprehensive examinations of both network and application layer vulnerabilities. Our analysts use commercial and publicly available tools - the same tools as the bad guys, in many cases, to achieve accurate and consistent results.
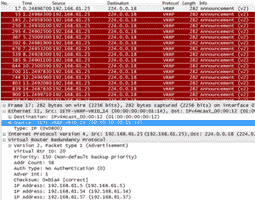
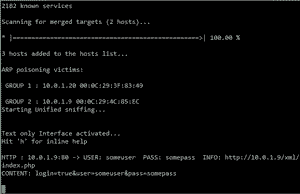
Internal Pentesting:
Internal Penetration Testing examines the security surrounding internally connected systems, typically within a corporate network. Just as External Penetration Testing tests the security of externally connected systems from over the Internet, Internal Penetration Testing involves the finding and exploitation of known and unknown vulnerabilities from the perspective of an inside attacker, whether that be a guest within the premises of an organization or disgruntled employee.
Our internal pentests are also designed to address advanced threats such as layer 2 and 3 protocols that, if successfully leveraged, can be exploited to gain additional access to a corporate network.
Pentests for Compliance:
Penetration Testing must be conducted to achieve compliance with a multitude of regulations and standards that industries face including the Payment Card Industry Data Security Standard (PCI DSS) [PDF]. These regulations require that penetration testing to be performed once a year and after any significant application modification or network upgrade.
WiFi Testing and Social Engineering:
While not required for compliance testing, many of our customers wish to evaluate the security surrounding their wireless networks - whether for guests or employees. Dara Security will test not only the encryption of your wireless network, but also perform a site survey, identify any rogue access points, and test to ensure proper segmentation is applied. Visitor or guest wireless networks without proper segmentation could allow an outsider access into your business environment.
Social engineering can be performed in a multitude of ways, however our preferred method is through electronic means, such as email and telephone. In a social engineering exercise, our analysts will attempt to solicit employees to supply privileged information, such as usernames or passwords, trade secrets or personal identifying information (PII). We can also passively collect information regarding users who open email attachments or visit potentially malicious websites controlled by Dara Security. Combined with a penetration test, this can offer a valuable evaluation of the human factor of your security program.
Experience:
Dara Security's analysts have over a decade of experience in various Profiling and Penetration Testing techniques. Our team's certifications include CISSP, GPEN, GXPN, GWAPT and certified web application penetration testing certifications. Our analysts are constantly studying and working to stay at the forefront of penetration testing and security assessment techniques as well as business trends through training, education, and speaking.

Vulnerability Tests:
Vulnerability Scans are security assessments that identify known network, operating system, web application and web server exploits & vulnerabilities with the use of automated tools. External vulnerability scans can give you an overall picture of the vulnerabilities present on your external network and assist in vulnerability risk management. In fact, these types of scans are required by several security and data protection mandates (PCI DSS/HIPAA) that may impact your organization. The needed frequency of a vulnerability scan can vary based on your environment. Many mandates require quarterly scanning.
External Testing:
Dara Security's External Vulnerability Scans find an organization's vulnerabilities and identifies the type and severity of the vulnerabilities. Even the best commercial vulnerability scanners can have a 40% false positive rate, on average, which is why Dara Security performs a validation of the findings from each scan. This helps eliminates false positives and gives you an actionable list of vulnerabilities to remediate.
Internal Testing:
Many organizations do not know the vulnerabilities present on their internal network. Dara Security's Internal Vulnerability Scans find an organization's vulnerabilities and identifies the type and severity of the vulnerabilities. Without knowing what vulnerabilities are present, it is impossible to mitigate those vulnerabilities and generate a baseline of internal systems. To prevent a data breach, the organization must verify that it is not exposed to security vulnerabilities which may aid an attacker in compromising the organization's data. Additionally, the type and severity of the vulnerabilities identified need to be defined to help prioritize remediation efforts and strengthen the organization's risk management program.
Expertise:
Dara Security security analysts are experts in vulnerability scanning. The same level of rigor required of an ASV scan is applied to all vulnerability scans Dara Security performs. Additionally, Dara Security uses only the best commercial security assessment tools available, constantly tested by our team, to give you the most accurate and reliable vulnerability scanning service available. Finally, recommendations for fixing vulnerabilities found during the scan are reviewed by Dara Security's testing team and remediation experts to ensure you get expert advice that takes into account the attacker's and defender's points of view.
Social Engineering:
While not required for compliance testing, many of our customers wish to evaluate the security surrounding their wireless networks - whether for guests or employees. Dara Security will test not only the encryption of your wireless network, but also perform a site survey, identify any rogue access points, and test to ensure proper segmentation is applied. Visitor or guest wireless networks without proper segmentation could allow an outsider access into your business environment.
Social engineering can be performed in a multitude of ways, however our preferred method is through electronic means, such as email and telephone. In a social engineering exercise, our analysts will attempt to solicit employees to supply privileged information, such as usernames or passwords, trade secrets or personal identifying information (PII). We can also passively collect information regarding users who open email attachments or visit potentially malicious websites controlled by Dara Security. Combined with a penetration test, this can offer a valuable evaluation of the human factor of your security program.
Penetration Testing:
Penetration Tests, or ethical hacking, are an important part of any security program. Our methodology, based largely on the Open Source Security Testing Methodology (OSSTM), is designed to validate the security surrounding externally connected systems from the Internet, as well as within a Corporate Network, depending on your needs.
Both External and Internal Penetration Tests are designed to detect weaknesses in a system, network or application that could allow host or information compromise and safely exploit these weaknesses to evaulate the impact on business operations.
External Pentesting:
External Penetration Testing involves finding and exploiting known and unknown vulnerabilities from the perspective of an outside attacker. External pentests can also test an organization's monitoring and incident response capabilities. Our testing is designed to mimic a variety of scenarios including a casual hacker who infiltrates a system for spam or other unrelated malicious purposes, dedicated hackers targeting with a specific goal and rogue employees or disgruntled ex-employees who may have privileged access or the ability to bypass certain access controls.
Using the Open Source Security Testing Methodology, our tests are comprehensive examinations of both network and application layer vulnerabilities. Our analysts use commercial and publicly available tools - the same tools as the bad guys, in many cases, to achieve accurate and consistent results.

Internal Pentesting:
Internal Penetration Testing examines the security surrounding internally connected systems, typically within a corporate network. Just as External Penetration Testing tests the security of externally connected systems from over the Internet, Internal Penetration Testing involves the finding and exploitation of known and unknown vulnerabilities from the perspective of an inside attacker, whether that be a guest within the premises of an organization or disgruntled employee.
Our internal pentests are also designed to address advanced threats such as layer 2 and 3 protocols that, if successfully leveraged, can be exploited to gain additional access to a corporate network.
Pentests for Compliance:
Penetration Testing must be conducted to achieve compliance with a multitude of regulations and standards that industries face including the Payment Card Industry Data Security Standard (PCI DSS) [PDF]. These regulations require that penetration testing to be performed once a year and after any significant application modification or network upgrade.
Experience:
Dara Security's analysts have over a decade of experience in various Profiling and Penetration Testing techniques. Our team's certifications include CISSP, GPEN, GXPN, GWAPT and certified web application penetration testing certifications. Our analysts are constantly studying and working to stay at the forefront of penetration testing and security assessment techniques as well as business trends through training, education, and speaking.
Wireless Network Testing:
While not required for compliance testing, many of our customers wish to evaluate the security surrounding their wireless networks - whether for guests or employees. Dara Security will test not only the encryption of your wireless network, but also perform a site survey, identify any rogue access points, and test to ensure proper segmentation is applied. Visitor or guest wireless networks without proper segmentation could allow an outsider access into your business environment.
Social engineering can be performed in a multitude of ways, however our preferred method is through electronic means, such as email and telephone. In a social engineering exercise, our analysts will attempt to solicit employees to supply privileged information, such as usernames or passwords, trade secrets or personal identifying information (PII). We can also passively collect information regarding users who open email attachments or visit potentially malicious websites controlled by Dara Security. Combined with a penetration test, this can offer a valuable evaluation of the human factor of your security program.
Penetration Testing:
Penetration Tests, or ethical hacking, are an important part of any security program. Our methodology, based largely on the Open Source Security Testing Methodology (OSSTM), is designed to validate the security surrounding externally connected systems from the Internet, as well as within a Corporate Network, depending on your needs.
Both External and Internal Penetration Tests are designed to detect weaknesses in a system, network or application that could allow host or information compromise and safely exploit these weaknesses to evaulate the impact on business operations.
External Pentesting:
External Penetration Testing involves finding and exploiting known and unknown vulnerabilities from the perspective of an outside attacker. External pentests can also test an organization's monitoring and incident response capabilities. Our testing is designed to mimic a variety of scenarios including a casual hacker who infiltrates a system for spam or other unrelated malicious purposes, dedicated hackers targeting with a specific goal and rogue employees or disgruntled ex-employees who may have privileged access or the ability to bypass certain access controls.
Using the Open Source Security Testing Methodology, our tests are comprehensive examinations of both network and application layer vulnerabilities. Our analysts use commercial and publicly available tools - the same tools as the bad guys, in many cases, to achieve accurate and consistent results.

Internal Pentesting:
Internal Penetration Testing examines the security surrounding internally connected systems, typically within a corporate network. Just as External Penetration Testing tests the security of externally connected systems from over the Internet, Internal Penetration Testing involves the finding and exploitation of known and unknown vulnerabilities from the perspective of an inside attacker, whether that be a guest within the premises of an organization or disgruntled employee.
Our internal pentests are also designed to address advanced threats such as layer 2 and 3 protocols that, if successfully leveraged, can be exploited to gain additional access to a corporate network.
Pentests for Compliance:
Penetration Testing must be conducted to achieve compliance with a multitude of regulations and standards that industries face including the Payment Card Industry Data Security Standard (PCI DSS) [PDF]. These regulations require that penetration testing to be performed once a year and after any significant application modification or network upgrade.
Experience:
Dara Security's analysts have over a decade of experience in various Profiling and Penetration Testing techniques. Our team's certifications include CISSP, GPEN, GXPN, GWAPT and certified web application penetration testing certifications. Our analysts are constantly studying and working to stay at the forefront of penetration testing and security assessment techniques as well as business trends through training, education, and speaking.
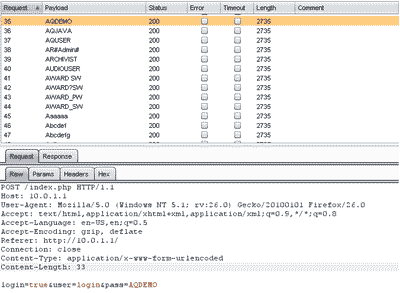
Web App Security:
As applications become more dynamic and user-friendly, the number of vulnerabilities left open by developers increases. To properly defend your organization from attacks, your web application must be solid.
Dara Security has found that more than 90% of attacks have come through the application layer. As a result, some industry regulations have made web application security assessment reviews mandatory. Specifically, the Payment Card Industry's Data Security Standard requires companies to perform application layer penetration testing (Requirement 6.6 [PDF]). Web Application Penetration Testing fulfills this regulatory requirement by examining all aspects of an application and pinpointing vulnerabilities.
Comprehensive Application Testing:
Our testing is designed to discover today's most prevalent and exploited web application vulnerabilities, and assist an organization in understanding the associated risks and business impact of the vulnerabilities. Unless requested otherwise, our web application penetration tests follow the OWASP methodology searching for serious exploits such as SQL Injection, Command Injection and Cross-Site Scripting (XSS). We also address lesser known threats such as Cross-Site Request Forgery, Clickjacking, Encoding Errors and DOM Injection.
Manual Testing:
In addition to automated tools, our team makes extensive use of manual testing. This type of testing is critical to find business logic flaws which automated tools cannot easily or accurately find. Manual testing focuses on finding vulnerabilities for the following layers and general security controls:
- Injection Flaws (such as SQLi, Command Injection)
- JavaScript and client-side Attacks (such as XSS, XST, CSRF)
- Authentication and Authorization
- Input Validation
- Account Harvesting
- Cryptography
- Error and Exception Handling
- Information Disclosure
- Cookie Attacks
- Session Hijacking
While "point-and-click" solutions will find obvious application flaws, our testing methodology constantly evolves to ensure the latest threats are identified and reported with a solution to address the vulnerability.
Experience:
Dara Security's certified GWAPT and CASS team members have been testing clients' web application security for nearly a decade. Offering web application penetration testing is one of our core services. Our experience and expertise has led us to follow a very detailed and structured methodology based on the OWASP Testing Guide for performing web application assessments. Dara Security uses the mindset and methodology of a hacker in an attempt to identify application misconfigurations and exploit vulnerabilities, ensuring a comprehensive approach to web application penetration testing.
Mobile App / Device Tests
Mobile Solutions:
With the increase in mobile application usage and the growth of mobile payment solutions, organizations now must extend the corporate network to include the end user devices running mobile applications. As a result, organizations now face new types of security threats directly related to mobile application usage.
Mobile Application Security:
With mobile applications, security testing is critical to identify vulnerabilities and mitigate threats. Dara Security's Mobile Application Security Testing is a full-scope approach consisting of:
- Mobile Application Penetration Test:
Our goal is to find flaws within the application that could provide access to sensitive information within the mobile application or that could allow an attack on other applications loaded on the same mobile device. - Mobile Application Source Code Review:
Our comprehensive review of the source code will help find vulnerabilities within the code and/or application design itself. Our all-inclusive approach includes manual code reviews, scripts and static analysis tools. We perform mobile app code reviews for Android, iOS and Windows platforms.
Mobile Device Security:
Our Mobile Device Attack & Penetration Assessment is an invasive look at the security of each mobile device connected to your network. We assess and evaluate your company's existing deployment of mobile devices and review any existing security controls and processes.
- Mobile Devices are rapidly being adopted by enterprises large and small
- Mobile Device Management (MDM) systems are usually never tested for security or configuration issues. The customer assumes the vendor has secured these systems
- Mobile Device Attack & Penetration can be performed anytime during an MDM deployment
We simulate a lost device and/or theft scenario to determine if your company's mobile devices can be attacked, and if your corporate data can be compromised as a result. We attempt simplistic device attacks (such as passcode bypass) as well as more advanced attacks (such as "Rooting" or "Jailbreaking") to achieve complete device compromise. In addition, we can test any third-party MDM system that you may have implemented as well as policies pushed to the device, ensuring that mobile devices have been deployed securely to your end user base.
How We Can Help:
Dara Security's purpose is to help organizations identify security threats in their own mobile applications or supplier mobile applications. Our in-depth threat analysis and business logic security testing is ideal for mobile applications involving sensitive data typically handled within mobile banking, mobile commerce and payment, and mobile healthcare applications.
Connect with Dara Security
Thank you for your interest in Dara Security. We look forward to helping you secure your data and achieve compliance.
© Dara Security 2025